Are you aware that your business’ IT infrastructure is vulnerable to cyber-attacks? And it does not matter if you have a small or big business.
The average cost to enterprises of data breaches reached $3.92 million. There were 4.1 billion recordsexposed in the first half of 2019. And 68% of business leaders say their cybersecurity risks are snowballing.
So, if you have not taken enough measures to beef up your security and protect your IT infrastructure from cyber-attacks, it is high time you take the matter seriously.
Here are some crucial steps you can implement to tighten your security and save your IT infrastructure from criminals.
1. Train your employees about work from home best practices
With so many businesses switching to work from the home model since the COVID-19 outbreak, it is crucial to train your employees concerning the best practices about work from home.
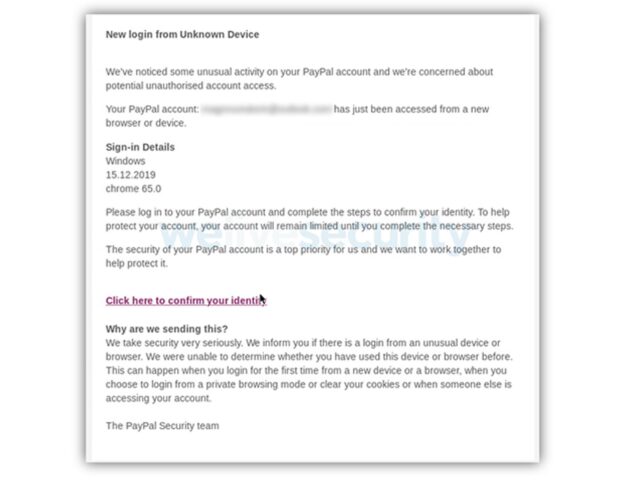
- Warn your employees of phishing emails: Ask them not to click on links in unsolicited emails. Scammers posing as people from reputed companies and organizations sending phishing emails are on the rise. Victims usually end up giving their financial and personal details, plus their login credentials. Below is an example of a phishing email.
- Ask your employees not to use public Wi-Fi: Your employees’ home Wi-Fi routers should be protected, and they should confirm the security of the devices used to get work accomplished. It is best to stick to corporate devices while accessing company data.
- Ask the employees to access SaaS apps via corporate network: Since almost all companies are using SaaS applications, remote workers should be accessing it only via the corporate network to ensure that your security solutions identify all traffic that accesses your services in the cloud.
2. Encrypt data with SSL certificate
When you install an SSL certificate, you will be able to secure information on your business website, including:
- Login passwords
- Payment information
- Personally identifiable information
- Proprietary information
- Legal papers and contracts
- Medical records
For making the secure communication between a web browser and a web server you should Use SSL encryption this will deterring third parties from accessing the information.
Though you may be a small business, you can still invest in affordable SSLs from reputed Certificate Authorities and safeguard your customer’s information. If you search for cheap SSL then, you will find many resellers out there like clickssl to secure single or multiple websites and unlimited subdomains and beef up your online security.
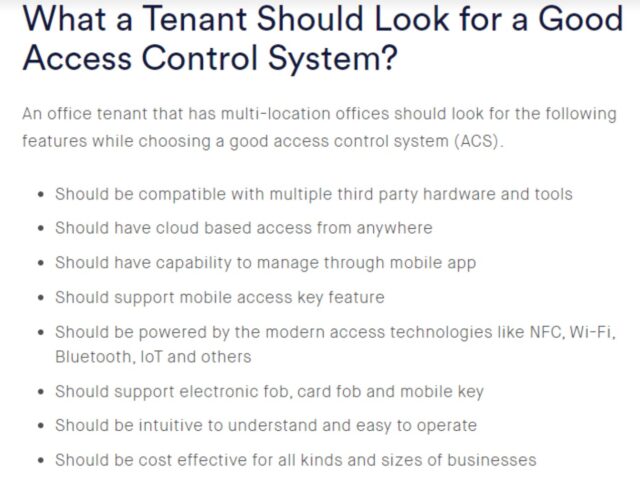
3. Implement an all-inclusive office tenant solution
If your office tenant has offices at several locations, come up with an all-inclusive office tenant solution that is integrated and controlled via one main server. By implementing this measure, you can monitor the satellite office security along with the remote office security in one amalgamated service.
4. Closely monitor your centralized management and analytics solution
Does your business use acentralized management and analytics solution? Monitor it closely.
Your analytics solutions should be able to track shadow IT. It brings risk to your organization, and your staff is your vulnerability. As perCisco, 83% of IT employees disclosed using illegal software.
Thus, it is essential to closely monitor and ask your employees to be transparent about using shadow IT.
5. Tweak your business’ email protection settings
As per the APWG’s Phishing Activity Trends Report for Q1 2024, month of March alone, more than 60,000 phishing sites were reported.
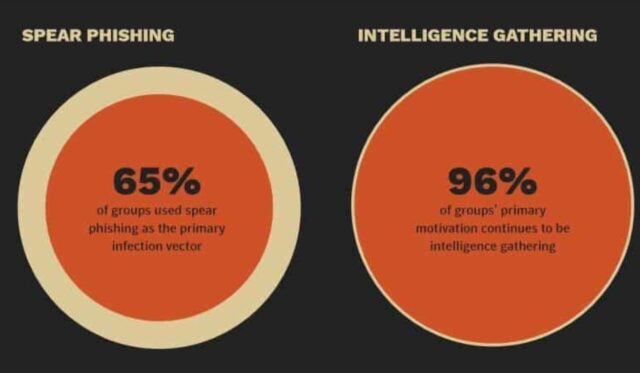
And Symantec’s Internet Security Threat Report 2019 says that spear phishing emails are utilized by nearly 65% of all known groups executing targeted cyber-attacks.
Be very watchful while getting unwanted emails. The best defense against phishing attacks is human intelligence.
Apart from avoiding clicking on suspicious links, set up your email spam folders for both outbound and inbound emails. This will keep unwanted emails at bay.
6. Practice router best practices for secure wireless networking
Some of the router best practices include:
- Changing the new device administrative pin.
- Hiding service set identifier (SSID) on the wireless access point.
- Using Wi-Fi Protected Access 2 (WPA-2) together with the Advanced Encryption Standard (AES) for encryption.
- Not making use of WEP (Wired-Equivalent Privacy).
- Not using the same network for your business account and guest Wi-Fi access.
7. Wipe all sensitive information before disposing of old devices
You might want to donate or throw away your old systems and devices. But be very careful before taking any step.
Before donating, wipe all crucial hard drive information and sensitive business data on flash drives, old CDs, or other old media.
Instead of throwing away, it is better to take the items to a company that will destroy them for you. Also, if there is any sensitive paper information, you want to get rid of, use a crosscut shredder to destroy them or burn them.
8. Use a password manager tool
Bad passwords are easily hacked. Do not use them. From among the 100 worst passwords of 2024, here are the top 20 passwords you should avoid.
If you find it difficult to remember complex passwords, there are password manager tools that can help you manage them and offer more security online.
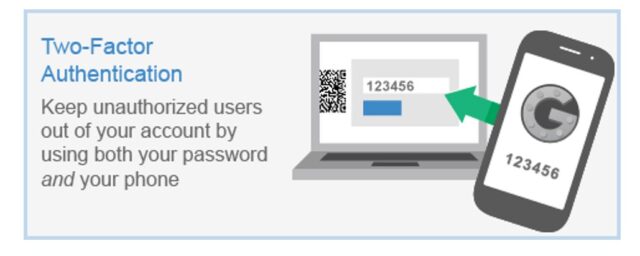
9. Use two-factor or multi-factor authentication
By using two-factor or multi-factor authentication, you can add extra layers of security to the standard password process of online identification.
Normally, you enter your username and password while logging in to your website. But, with two-factor, you will be required to enter your Personal Identification Code or password. Sometimes, you will be using your fingerprint.
If you use multi-factor authentication, you will be asked to enter more than two authentication methods apart from your username and password.
Even if hackers crack your password, if your site is using two-factor or multi-factor authentication, they will not be able to compromise it.
Wrapping Up
Note that these 9 steps are not the be-all and end-all for security practices. They do not guarantee that your IT infrastructure will never be attacked by cyber attackers. But it will highly minimize the chances of your IT infrastructure getting compromised.
Do not let your negligence or carelessness entice cybercriminals to attack you. Be smart and keep up to date with the latest security protocols. And remember that human intelligence can be the best defense against many cyber-attacks.